Risks of Staking Crypto: A Guide for Investors
Discover the risks of staking crypto and learn how to protect your investments. A must-read guide for anyone looking to stake crypto safely.
Oct 19, 2025
generated
risks of staking crypto, crypto staking, slashing risk, DeFi risk management, proof of stake

Crypto staking can be an effective method for generating yield on digital assets, but it is crucial to recognize that it is not a risk-free endeavor. Any assertion that staking offers guaranteed returns without downside is an oversimplification. In reality, staking involves a unique set of risks that every allocator—from retail investors to institutions—must understand before committing capital.
The primary risks can be categorized into four key areas: technical risk, such as validator slashing; market risk, particularly during lock-up periods; counterparty risk associated with staking providers; and the evolving regulatory landscape.
Understanding the Core Risks of Crypto Staking
Staking is often presented as a source of passive income. While this is a key part of its appeal, equating it with a traditional high-yield savings account is a critical error. Staking is an active financial commitment where capital is exposed to protocol-level and operational risks not typically found in traditional finance.
From the integrity of the underlying smart contract code to the operational security of a third-party staking service, the risks are layered and complex. A thorough understanding of these factors is the first step toward building a durable and risk-aware staking strategy.
This infographic outlines the main risk categories and their interdependencies.
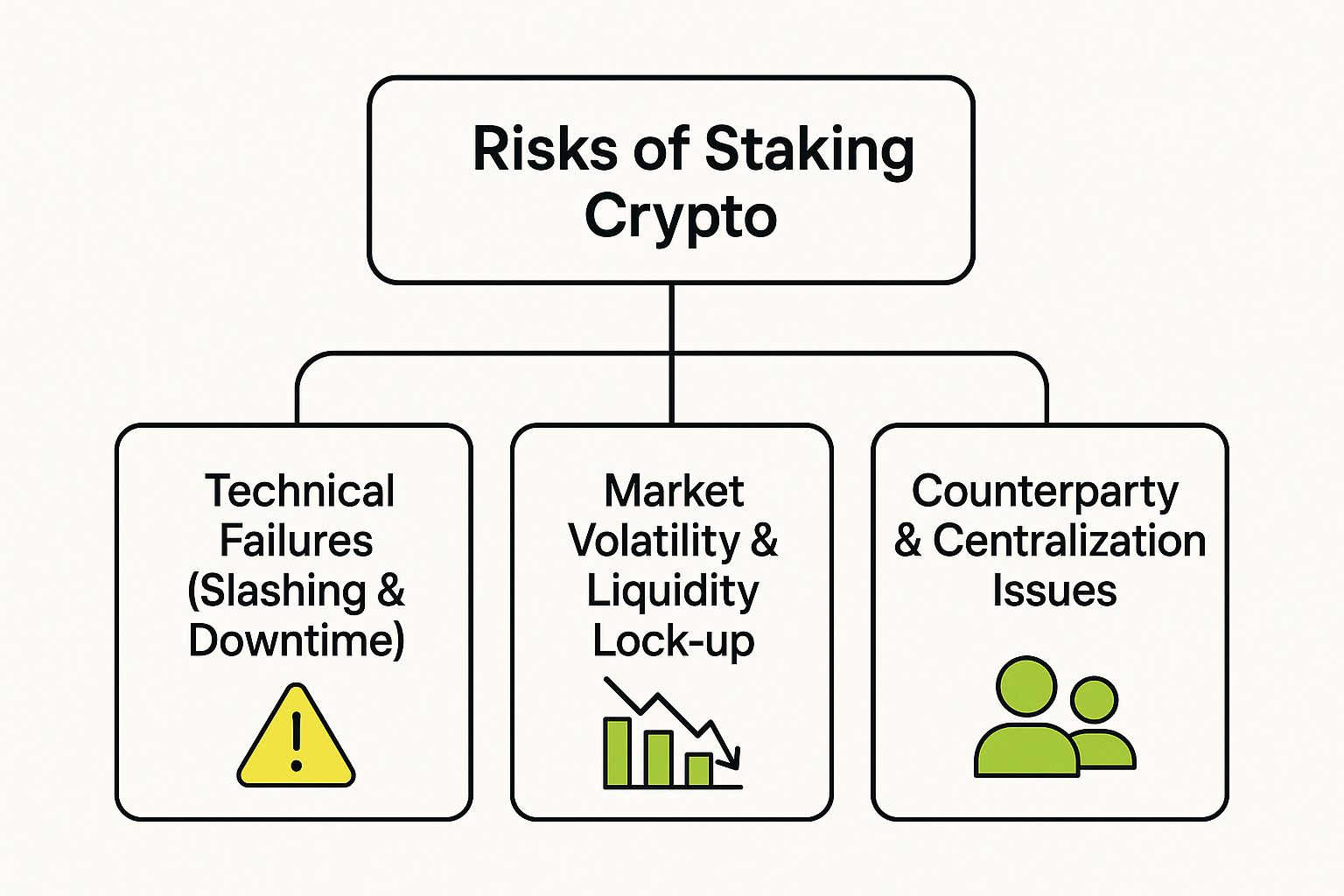
As illustrated, these are not isolated issues. They form a web of interconnected factors that can compound, which is why a comprehensive, holistic approach to due diligence is non-negotiable for any serious allocator.
To provide a clear framework, here is a summary of the primary risk categories that require careful consideration.
| Key Staking Risk Categories at a Glance |
| :--- | :--- | :--- |
| Risk Category | Primary Concern | Potential Investor Impact | | Technical Risk | Protocol bugs, smart contract vulnerabilities, or validator errors (downtime, double-signing). | Loss of staked capital through "slashing" penalties or hacks; missed rewards. | | Market Risk | Asset price volatility combined with protocol-enforced lock-up or unbonding periods. | Inability to sell assets during a market downturn, leading to significant unrealized losses. | | Counterparty Risk | The staking provider (exchange, pool) suffers a hack, becomes insolvent, or acts maliciously. | Complete loss of staked funds if the provider is compromised or fails. | | Regulatory Risk | Governments may reclassify staked assets as securities or impose new rules on staking providers. | Forced liquidation of positions, compliance burdens, or a sudden shutdown of staking services. |
Each of these categories warrants a detailed analysis, as the nuances are critical. A single vulnerability in one area can cascade and impact the others, transforming a minor issue into a significant capital loss.
The Interplay of Staking Risks
Consider a practical example of risk contagion. A technical failure, such as a validator going offline, can trigger a financial penalty known as slashing. If this occurs during a significant market downturn, the situation worsens. Because the assets are locked, the investor is unable to exit the position to mitigate losses, even with the knowledge that their chosen validator is underperforming.
This is where counterparty risk introduces another layer of complexity. When staking through a centralized exchange or a DeFi protocol, an investor is entrusting their capital to the provider's security infrastructure, operational competence, and financial stability.
"One of the biggest risks to the Ethereum L1," as described by its co-founder Vitalik Buterin, is the centralization that can arise from large staking pools and providers. This concentration of power can introduce systemic risks that affect the entire network.
This is a crucial point. It demonstrates that the business and operational decisions of a few large entities can have broad market effects, impacting not only their clients but the integrity of the entire blockchain ecosystem.
Throughout this guide, we will analyze each of these categories, providing a clear framework to assess and mitigate the real risks of staking crypto.
Decoding Technical Risks: Slashing and Downtime
Beyond market fluctuations, some of the most significant staking risks are embedded directly within a network's protocol. These are rules designed to ensure network security, but they can negatively impact an investment if operational standards are not met.
Central to this technical risk is a mechanism called slashing. This can be understood as an automated penalty system for the blockchain. When a validator—the node responsible for confirming transactions and proposing new blocks—acts maliciously or negligently, the network automatically penalizes them by confiscating a portion of their staked assets.
If you have delegated your stake to such a validator, their operational failure results in your financial loss.

Common Triggers for Slashing Penalties
The two primary infractions that result in slashing are extended validator downtime and double-signing (validating two different blocks at the same height). The network interprets both as serious threats to its integrity.
Validator Downtime: If a validator's server crashes or loses its connection for a prolonged period, it fails to perform its duties. The network flags this as unreliability. The resulting penalty is typically minor, often resulting in missed rewards rather than a loss of principal.
Double-Signing: This is a more severe offense. It occurs when a validator signs two different blocks at the same point in the blockchain's history, effectively creating conflicting versions of the transaction ledger. Networks treat this as a malicious act and impose significant slashing penalties.
When a validator is penalized, so are the delegators who staked with them. This is an automated enforcement mechanism on proof-of-stake (PoS) blockchains designed to hold operators accountable. This has occurred on networks like Ethereum, where validator errors have led to tangible financial losses for stakers. A slashing event can reduce principal by 0.5% to several percentage points instantly, highlighting the importance of validator selection. If you are still evaluating the fundamental trade-offs, you can delve deeper into the staking vs. holding debate on materialbitcoin.com.
Vetting Validators to Mitigate Technical Risk
Because your capital is at stake, conducting due diligence on a validator is a critical step. This is especially true for HNWIs and institutional investors who require robust operational security. By delegating, you are effectively outsourcing security and performance to a third party.
A validator's history is the best predictor of its future performance. Scrutinizing their track record for uptime, previous slashing incidents, and community reputation provides a clear view of their reliability and technical competence.
When evaluating a potential validator, focus on these key metrics:
Uptime History: Look for a demonstrated uptime of 99% or higher. Anything less may indicate unreliable infrastructure.
Slashing Record: A history free of slashing incidents is the ideal standard. Any past events require thorough investigation.
Commission Fees: Ensure fees are competitive and transparently disclosed, as they directly impact your net yield.
Community Standing: A strong reputation within the network's community is a valuable indicator. Review forums and other channels for feedback from other stakers.
By conducting a meticulous evaluation, you can significantly reduce exposure to technical risks and protect your principal from what are often avoidable penalties.
Navigating Market and Liquidity Risks
Beyond the technical protocol rules, staking carries financial risks familiar to any allocator, but they are amplified in the crypto markets. Staking involves a combination of market risk and liquidity risk, which can significantly impact a portfolio during periods of high volatility.
The core issue is that assets are often locked and inaccessible precisely when the need to sell may be highest.

The most evident financial risk is price volatility. For example, a 5% annual percentage yield (APY) on a staked asset offers little protection if the asset's price declines by 20%. Because the capital is locked, the investor cannot exit the position to preserve capital, turning a paper loss into a locked-in, unrealized loss.
This inability to react leads to the second, closely related challenge: liquidity risk. Nearly all Proof-of-Stake networks mandate "unbonding" or "lock-up" periods when an investor decides to unstake. This is a network security feature designed to maintain stability, but it renders capital illiquid for a defined duration.
Understanding Lock-Up Periods
These lock-up periods are a critical component of the risk equation and must be understood before staking. They vary significantly between protocols, from a few days to several weeks, and create a major obstacle for active risk management.
An investor observing a sudden market decline is left powerless during this unbonding period.
For example, Ethereum's protocol includes a mandatory unstaking queue that can last for days or even weeks, depending on network congestion. This severely constrains the ability to exit a position rapidly. This lack of flexibility becomes extremely costly during a market downturn, potentially amplifying losses. Given that a large percentage of many major tokens are staked at any time, a vast amount of capital is subject to these constraints, and investors who disregard them may face liquidity shortages.
The Rise of Liquid Staking Derivatives
To address this liquidity challenge, liquid staking derivatives (LSDs) have emerged as a popular solution. The mechanism is straightforward: an investor stakes through an LSD provider and receives a tradable token (e.g., stETH for ETH) that represents their staked position. This token can be sold, traded, or used in other DeFi applications, restoring liquidity to the asset holder.
However, LSDs introduce their own distinct and complex risks:
De-Pegging Risk: The value of the derivative token is not guaranteed to maintain a 1:1 peg with the underlying asset. During periods of market stress or if confidence in the provider diminishes, the LSD may trade at a discount. Selling during such a period would result in a capital loss.
Smart Contract Risk: LSDs are built on complex smart contracts. A bug, exploit, or vulnerability in the code could lead to a complete and irrecoverable loss of the underlying staked assets.
A firm understanding of liquidity in cryptocurrency is essential before utilizing these more sophisticated instruments. While LSDs provide an innovative solution to lock-up periods, they also introduce new layers of technical and market risk that require rigorous due diligence.
Evaluating Counterparty and Centralization Risks
Beyond the protocol itself, the choice of staking provider introduces a significant layer of risk. The decision of how to stake—whether through a centralized exchange, a decentralized pool, or by running a private validator—directly influences your exposure to critical threats. Each method presents a unique set of trade-offs.
When you delegate assets to a third party, you assume counterparty risk. This is the fundamental risk that the other party in a transaction will not fulfill its obligation. In the context of a centralized finance (CeFi) platform, this could manifest as insolvency, a security breach, or mismanagement of user funds, any of which could lead to a total loss of capital. Our guide on what is counterparty risk explores this topic in greater depth.
Decentralized finance (DeFi) staking pools are not immune to such risks. While they mitigate the risk of a single corporate failure, they introduce their own vulnerabilities. A bug or exploit in a DeFi protocol's smart contract can be equally devastating, potentially enabling an attacker to drain all staked assets.
The Systemic Threat of Centralization
A more subtle but equally potent risk is centralization. When a small number of large staking providers—be they exchanges or liquid staking protocols—control a significant majority of a network's staked assets, it threatens the integrity and decentralization of the blockchain itself. Ethereum co-founder Vitalik Buterin has identified this concentration as "one of the biggest risks" facing the network.
This level of centralization creates massive single points of failure. If one of these dominant players experiences a critical bug, security breach, or regulatory action, the impact could be catastrophic for the entire network, not just their direct clients. In such worst-case scenarios, understanding the steps to recover stolen cryptocurrency can be a valuable contingency.
The core problem with staking centralization is that economic pressures can lead to a "rich get richer" dynamic. The biggest pools attract the most capital, which further cements their power and influence over the network.
A Framework for Vetting Staking Providers
For any serious allocator, from HNWIs to institutional funds, conducting thorough due diligence on a staking provider is an essential risk management practice. A clear framework is needed to assess their operational resilience and trustworthiness. Before committing capital, rigorously evaluate the following factors:
Security Audits: Has the provider undergone multiple, recent security audits from reputable firms? Review these reports for any unaddressed critical vulnerabilities.
Operational History: Analyze their track record. A long history of consistent uptime and zero slashing incidents is a strong positive indicator.
Transparency and Reporting: Does the provider offer clear, real-time data on performance, fees, and validator node health? A lack of transparency is a significant red flag.
Fee Structure: Are all fees, including commissions and any potential hidden costs, clearly disclosed? An opaque fee structure can erode net yield over time.
Understanding Regulatory and Tax Complexities
Beyond technical and market risks, a significant challenge in staking arises from the evolving regulatory and tax environments. For professional allocators—including HNWIs, family offices, and institutions—these are not minor details but material liabilities that can impact financial outcomes.
The core of the issue is ambiguity. In most major jurisdictions, the legal classification of staked assets and their generated rewards remains a grey area. Regulators have yet to establish clear, consistent rules, leaving investors to navigate a complex landscape of interpretations and potential enforcement actions. The primary concern is that regulators could classify certain staking arrangements as securities, which would trigger a host of registration and compliance requirements.
This uncertainty poses a significant challenge for professional allocators who rely on legal clarity and predictability.
The Looming Question of Securities Classification
The debate over whether staked assets or staking-as-a-service offerings constitute securities is ongoing. If regulators determine that a particular staking program meets the criteria of an investment contract, the consequences could be significant.
For Staking Providers: Platforms could face enforcement actions, fines, and mandates to register with securities commissions, fundamentally altering their business models.
For Investors: A securities classification could retroactively challenge the legality of past staking activities and impose complex new reporting obligations.
This regulatory overhang means the rules could change with little notice, potentially forcing the liquidation of positions or causing the shutdown of popular staking services.
The key takeaway here is that regulatory risk is always in motion. A staking strategy that’s perfectly compliant today might get reclassified tomorrow. You have to keep your ear to the ground constantly.
Navigating the Tax Maze
The tax treatment of staking rewards introduces another layer of operational complexity. In many jurisdictions, rewards are considered taxable income at the moment they are earned, based on their fair market value at that time. This creates a significant tracking and reporting burden.
Consider that rewards may be distributed in small increments on a daily or even more frequent basis. Each distribution is a taxable event, requiring meticulous record-keeping to calculate the cost basis for thousands of micro-transactions. Without specialized software, this can become an overwhelming administrative task.
Incorrect reporting can lead to significant tax liabilities and penalties. For any serious staking operation, accurate tax compliance is non-negotiable.
Building Your Risk Mitigation Framework
Synthesizing this information is key. Awareness of technical, market, and counterparty risks is the first step; translating that awareness into a coherent strategy is the next. Building a resilient staking portfolio is not about eliminating all risks—an impossible task—but about managing them intelligently.
This requires a deliberate, structured approach rather than simply pursuing the highest advertised annual percentage yield (APY).
The cornerstone of this approach is diversification. This extends beyond holding different crypto assets. In staking, it means distributing capital across multiple, non-correlated validators. Concentrating all funds with a single validator, even a reputable one, creates an easily avoidable single point of failure. The same principle applies to platforms: diversifying across different staking providers can insulate a portfolio from the failure or compromise of a single service.
Key Pillars of a Staking Risk Strategy
A robust risk management framework should be built on three pillars that directly address the primary risks discussed. Each requires careful consideration and ongoing monitoring.
Diversification: Allocate funds across several validators. Furthermore, diversify the types of providers used. For example, an allocation could be split between a centralized service (for simplicity) and a decentralized liquid staking protocol (to maintain liquidity and mitigate censorship risk). A well-structured approach to staking as a service can facilitate this type of diversification.
Diligent Vetting: Never delegate to a provider without conducting thorough due diligence. This is not optional. Investigate their security audits, review their historical uptime and slashing record, and ensure full transparency on their fee structure. If a provider is reluctant to share operational details, it should be considered a major red flag.
Strategic Allocation: This involves balancing trade-offs. Carefully weigh the potential yield against lock-up periods and liquidity constraints. Higher yields are almost always associated with longer lock-ups or exposure to newer, less-proven protocols. Ensure your staking allocations align with your investment horizon and liquidity needs. Being locked into an illiquid position during a volatile market is a critical risk to avoid.
A well-defined risk management plan transforms staking from a speculative gamble into a calculated investment strategy. It shifts the focus from chasing short-term gains to building a sustainable, long-term position.
Ultimately, a proactive stance on risk management is what separates successful stakers from those who suffer preventable losses. To explore this topic further, consider mastering risk management in investing.
Frequently Asked Questions
Engaging in crypto staking often raises several key questions. Below are answers to some of the most common concerns allocators have when evaluating these risks.
Can I Lose All My Money Staking Crypto?
Yes, a total loss of principal is possible. While not the most frequent outcome, it is a risk that cannot be disregarded. A single slashing event typically results in a small percentage loss of principal, but a convergence of multiple risks could lead to the loss of an entire stake. This scenario is one of the more severe risks of staking crypto.
For example, a critical vulnerability in a DeFi staking protocol's smart contract could be exploited by an attacker, potentially resulting in the complete drain of all staked funds. Similarly, if a centralized exchange used for staking suffers a catastrophic hack or becomes insolvent, user assets could be lost permanently. This underscores why rigorous due diligence and diversification are essential defensive measures.
Is Staking Safer Than Trading?
Comparing the safety of staking versus trading is like comparing two different risk profiles; they are not directly equivalent. Staking is often perceived as "safer" because it may seem less exposed to short-term market timing pressures. However, it involves substituting one set of risks for another. Trading risk is primarily centered on market volatility and execution timing.
Staking, conversely, introduces a different array of risks:
Technical Failures: A validator could experience downtime, leading to slashing penalties.
Protocol Vulnerabilities: Smart contracts may contain undiscovered flaws that can be exploited.
Liquidity Constraints: Lock-up periods can immobilize capital, preventing risk management during market downturns.
Counterparty Risk: The chosen platform or validator could fail or be compromised.
Neither activity is inherently "safer." They simply require different frameworks for risk assessment and management.
An effective investment strategy isn't about finding a "risk-free" option but about clearly identifying the specific risks you are willing to accept and building a framework to manage them.
How Do I Choose A Safe Staking Validator?
Selecting a reliable validator is the primary defense against slashing risk. Begin by researching their track record, looking for consistent, high uptime—ideally above 99%.
Next, investigate their slashing history; a clean record is a strong indicator of operational competence. Confirm that their commission rates are fair and transparently disclosed. Finally, assess their reputation and engagement within the network's community. It is also prudent to consider diversifying away from the largest validators. Allocating a portion of your stake to smaller, high-performing validators contributes to network decentralization, which reduces systemic risk for all participants.
Ready to cut through the noise and find institutional-grade BTC and stablecoin investment products? Fensory provides the data-driven discovery and analytics platform that serious allocators need. Explore curated strategies and perform due diligence with confidence at fensory.com.